News: The German National ID goes Mobile
German citizens will soon be able to carry their national electronic ID (eID) on certain smart phones thanks to work being done by Samsung, Deutsche Telekom and the German government’s Office for Information Security. The solution involves cloning the eID smartcard ― which is NFC-enabled ― onto the phone’s secure element.
It’s the latest in a steady progression of digitization of the German national identity system.
The same evolutionary story is evident across many different types of credential. A credential classically starts life as a paper card, and progresses in stages through passive data carriers and “smart” cards, with some eventually appearing in smart phones. This lineage has played out in near-identical fashion (albeit at different rates) with credit cards and driver licences.
A Maturity Model for Data Carriers
In this article I map the progressive digitisation of digital credentials onto the familiar five stage Capability Maturity Model (CMM). By showing how the pattern is repeatable, perhaps we can accelerate the modernisation of other credentials and enjoy the benefits of usability and fraud resistance more widely.
I’ve written in more detail elsewhere about the evolution of data carrier technology. In short, steady improvements ― firstly in data storage and then around cryptography ― have seen active or “smart” devices emerge with the ability to present verified data about their individual holders. In retail payments, smartcards now dominate. What makes a smartcard smart is its ability to prove cryptographically that the cardholder was in control of a transaction. The person’s knowledge of a PIN or their possession of a biometric can be verified (matched) on the card itself. Not only that but each separate transaction is digitally signed by a private key within the chip unique to the cardholder, thus cryptographically marking the transaction as original. And furthermore, the cardholder data carried by the chip has been digitally signed (that is, certified) by the card issuer, in effect branding the account details and imparting them with provenance. The bundle of transaction details and cardholder account number produced each time a chip card is used carries forward the imprimatur of the issuer and cannot feasibly be counterfeited.
The stages of data carrier evolution can be compared with the five levels in the standard CMM framework. I propose the following five levels of Data Carrier maturity:
Level 1: Human Readable. Carries plain text account holder details; historically printed on paper, perhaps with a watermark, the issuer’s autograph and/or an official seal; data transcribed by hand by the receiver.
Level 2: Machine Readable. Carries data in some sort of memory, so it can be automatically transferred to a terminal, usually via magnetic stripe or bar code; data transfer is passive, reading from the card and writing to the terminal. The ISO 7816 plastic card specification and the magnetic stripe customer data coding standards of the American Bankers Association were widely adopted across many industries.
Level 3: Signs of Origin. Data carrier has provenance features such as holograms and optically variable printing to frustrate copying or counterfeiting. A prototypical digital provenance feature was the CVV (Card Verification Value) printed on the back of a credit card, which was originally used to evince originality when details are read out by the cardholder over the phone. The CVV wasn’t left behind on the carbon copies resulting from normal manual card processing and was therefore less accessible to the early “dumpster diving” ID thieves.
Level 4: Cryptographically Verified. PIN (or biometric) match proves customer control. Digital signatures prove originality in two ways: cardholder data is signed (i.e. certified) by the device issuer, and each transaction is also signed in the chip to prevent transaction replay or counterfeiting. A smartcard won’t talk to unapproved terminals, which prevents card skimming and cloning.
Level 5: Intelligent / Adaptive. Smart phones have the processing power and diverse sensors to capture rich signals about the device in use, such as user behaviour, transaction history and geolocation. The device software can apply complex permissions management to control what the user can do, and look for anomalies that might indicate misuse or abuse.
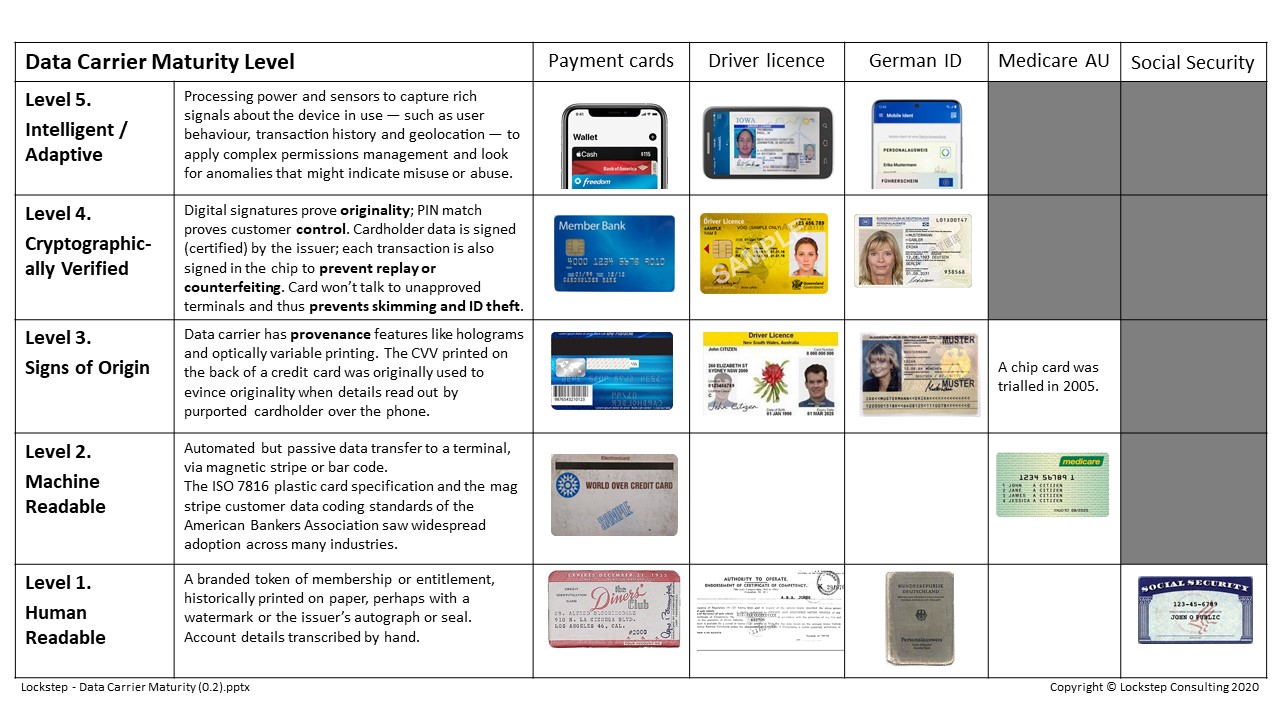
Let’s now track progress in different industries.
Banking
The credit card industry has led the progressive adoption of more robust data carrier technologies (all the while keeping the network business model, merchant service agreement and cardholder agreements more or less constant). It seems that rapid digitisation in retail banking has driven the release of smartphone wallets like Apple Pay and Samsung Pay and the attainment of Data Carrier maturity level 5.
Historically, it is noteworthy how the banking sector also forged the plastic card standards (at Data Carrier maturity levels 2 and 3) that have permeated identity use cases across so many other industries: employee IDs, student cards, driver licensing, mass transit ticketing, club membership, library cards, loyalty and government ID.
Driver licensing
Driver licences have advanced from fragile pieces of paper to plastic cards in most parts of the world. As licences morphed into de facto identity documents, they became targets for counterfeiting by organised crime, and so Level 3 anti-fraud features have become ubiquitous, such as holograms, optically variable printing and guilloche engraving.
In Australia, the state of Queensland introduced a chip into their driver licence over ten years ago. In 2019 New South Wales was the first Australian state to roll out a Digital Driver Licence option for smart phones, while many licensing authorities worldwide are doing the same, and the International Organisation for Standardisation is drafting a Mobile Driver Licence (mDL) ISO standard including NFC technology for secure data presentation.
Social Security in Australia and the U.S.A.
Australia’s universal public health insurance scheme Medicare has used a plastic card with magnetic stripe for decades. Over 2004-06 a small pilot of a Medicare smartcard was undertaken in the state of Tasmania. At first the objectives were simply to upgrade the mag stripe to make the card more difficult to clone or counterfeit. That initiative was then subsumed into a larger “Access Card” proposal with the broader and far more complex mission to rationalise a number of social security accounts and reorganise all accounts within a new national Human Services administration. The Access Card attracted widespread protests for its resemblance to a national identity, something most Australians have long resented. In 2007, a change of federal government saw the smartcard abandoned (at around the same time as the British government cancelled its national ID card project).
No administration in Australia has ever returned to the worthy idea of simply upgrading the Medicare card from mag stripe to chip for better fraud resistance, and the card remains at Data Carrier Maturity Level 2.
In the U.S., multiple proposals to introduce “Common Access Card” technology (that is, the defence force smartcard) into the Medicare system have come and gone over the years. The Social Security card has, notoriously, yet to advance past Data Carrier Maturity Level 1.
Conclusion: Smart Data Carriers and Data Quality
To summarise, chip cards (at Level 4) and the secure elements of smart phones (at Level 5) fundamentally protect the quality of critical data, as follows:
- Provenance: the user’s details are certified by the issuing authority through a digital certificate bound to the chip
- Consent: each fresh transaction is digitally signed ― automatically and seamlessly ― for the user, using a private key unique to them held in the chip.
- Possession: the fact that the card or smartphone was unlocked by a PIN or biometric proves to a reasonable degree of confidence that the device was in the possession of its rightful user when the transaction was originated
- Privacy: the accuracy and provenance of user data presented from a cryptographic chip makes the transactions reliable without further extraneous identification and exposure of personal data.
- Originality: provenance and proof of possession allow a relying party to tell the difference between original Personal Data and data that has been counterfeited or stolen and replayed.
With Data Carrier Maturity Level 5 now well established in banking and driver licensing, this benchmark can be taken up in all sectors where mission-critical identifiers are an integral part. Healthcare and social security are long overdue for better protection of individuals’ bona fides. While privacy anxieties have dominated in these areas, the Data Carrier Maturity Model shows how IDs and personal details can remain appropriately siloed and secure when upgrading to superior technologies. And the uniform user experience of mobile credentials ― cryptographically verified by sophisticated algorithms that are standard under the covers ― can be naturally extended to all walks of life.
Gratitude
Thanks to George Peabody at Glenbrook Partners for pointing me to the German mobile eID report, and for another sparkling conversation recently which helped further my thinking on identity, data, data quality, and data carriage. At times like this, I appreciate my network more than ever.


