- 30% of US and UK remote workers say their organizations don't require them to use a secure access tool, including VPN, to log into corporate databases and systems, according to Ivanti's 2021 Secure Consumer Cyber Report.
- Plus, 25% of remote workers in the US and UK aren't required to have specific security software running on their devices to access certain applications while working remotely.
- And one in four US remote workers use their work email and passwords to log in to consumer websites and apps.
Cybersecurity gaps have continued to widen during the pandemic. A noteworthy survey by Ivanti illustrates exactly how remote workers are putting organizations at risk and where enterprise security is falling short, making those cybersecurity gaps challenging for CISOs to close. Ivanti's 2021 Secure Consumer Cyber Report outlines the challenges that cybersecurity and IT teams have faced when securing remote workers in what’s being described as the “Everywhere Workplace.” Based on interviews with more than 2,000 US and UK respondents working from home in November 2020, the survey shows that authentication and endpoint security needs to improve across all devices that employees use.
IT Organizations Need Help Closing Their Cybersecurity Gaps
Of the many lessons learned from 2020, among the most valuable are how virtual workforces need self-diagnosing and self-remediating endpoints, while IT organizations need improved unified endpoint management (UEM) as part of a zero-trust strategy. Bad actors continue to target remote workers' privileged access credentials to gain access and exfiltrate customer, financial and proprietary data, including intellectual property. Ivanti's survey provides insights into where cybersecurity gaps need attention first:
The most challenging threat surface to protect is a person's identity because it's exposed across so many threat surfaces, including personal and work devices, consumer websites, and IoT devices in homes. The pandemic is proving identities are the new security perimeter. A person's cell phone, personal tablet, and laptop is a real-time digital definition of a person's identity. Nearly half (49%) of US remote workers use personal devices for their jobs, often without two-factor authentication enabled. The graphic below shows how organizations can close this cybersecurity gap by adopting UEM as part of their go-forward initiatives in 2021 and beyond:
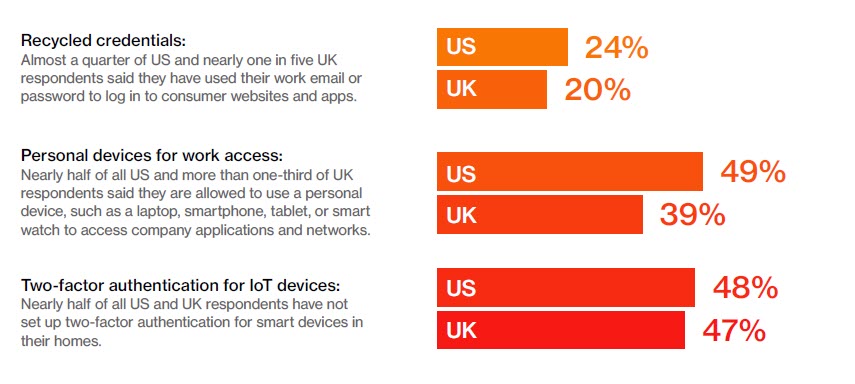
Lack of consistent security software and password standards is a big contributor to US and UK organizations' cybersecurity gaps today. One in four remote workers can access enterprise resources without any security software in place. An even more surprising finding is that 30% of remote workers in the US and UK can access corporate data without a secure access tool or VPN connection. If a remote worker’s identity is compromised, there's a one in three chance that their organization will be breached, enabling cyberattackers to move laterally through the company’s systems:

Protecting remote workers' identities & devices at scale requires Zero Trust. Automating as many tasks as possible while providing a continuous and seamless user experience is the surest way to close cybersecurity gaps. Getting rid of passwords and automating two-factor authentication using Zero Sign-On (ZSO), a core part of the Ivanti platform, is proving essential today. Zero Sign-On relies on proven biometrics, including Apple's Face ID, as a secondary authentication factor to gain access to work email, unified communications and collaboration tools, and corporate-shared databases and resources. CISOs and their teams also need to consider how mobile threat defense can secure personal devices against phishing, device, network, and malicious app threats.
In conclusion, enterprise cybersecurity gaps are widening due to a combination of risky consumer behavior and a lack of consistent security for mobile workforces. And these gaps will only increase as employees increasingly work from anywhere, using their personal devices to connect to corporate resources. To secure and enable the future of work, organizations need to start implementing and maturing an end-to-end zero trust security model today by leveraging new technologies and protecting their current security technology investments.


