
How many data breaches were reported in 2016? Even if you're under the impression it was a lot, the number may still surprise you: Nearly 3,000, encompassing 2.2 billion records, as ZDNet reports.
Affected companies and organizations included LinkedIn, VK.com, the National Security Agency and most infamously of all, Yahoo, which reported that 500 million user accounts had been compromised.
Add in high-profile DDoS (distributed denial-of-service) attacks such as the one committed by the IoT botnet Mirai against DNS provider Dyn, and the events of 2016 should make cybersecurity a top priority and topic of discussion for the tech industry this year.
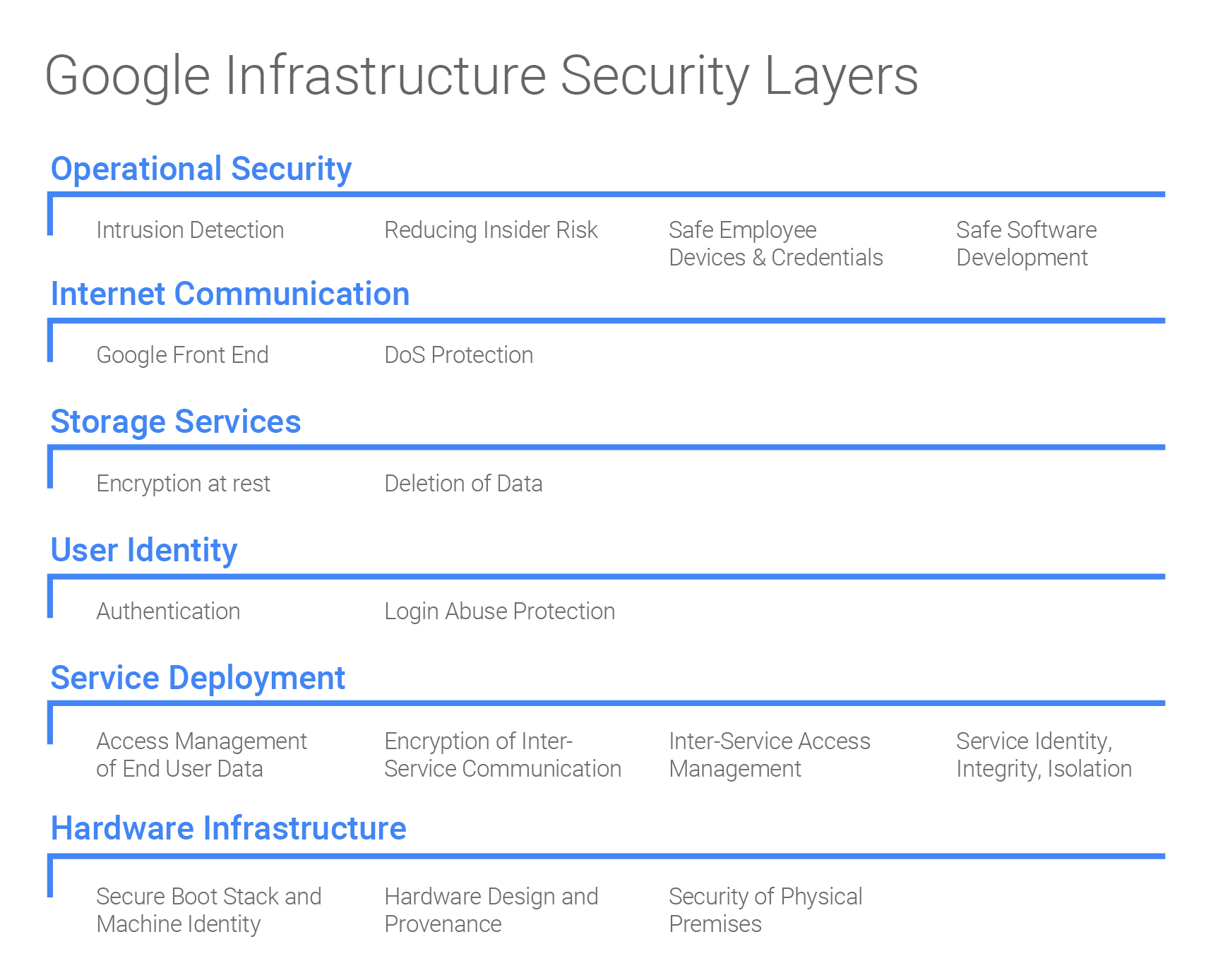
To that end, Google has just provided a significant measure of transparency into its own cybersecurity practices with the publication of a document titled "Google Infrastructure Security Design Overview." While stopping short of providing any technical secrets, the document paints a detailed picture of Google's approach to security for both its consumer and enterprise cloud services.
(Credit: Google)
The document is large enough to make a brief summary difficult, but some of the highlights include Google's description of its physical security measures. Let's just say Google's server racks are protected by more than a locked cage:
Google designs and builds its own data centers, which incorporate multiple layers of physical security protections. Access to these data centers is limited to only a very small fraction of Google employees. We use multiple physical security layers to protect our data center floors and use technologies like biometric identification, metal detection, cameras, vehicle barriers, and laser-based intrusion detection systems. Google additionally hosts some servers in third-party data centers, where we ensure that there are Google-controlled physical security measures on top of the security layers provided by the data center operator. For example, in such sites we may operate independent biometric identification systems, cameras, and metal detectors.
Google is also using proprietary security chips in its hardware, something which was previously not publicly known:
We also design custom chips, including a hardware security chip that is currently being deployed on both servers and peripherals. These chips allow us to securely identify and authenticate legitimate Google devices at the hardware level.
"Bravo Google," says Constellation Research VP and principal analyst Steve Wilson. "The hardware security they mention is really reassuring. Most of the security problems we have can be related to the fact that software is too soft. It's too easy for an attacker to read software from computer memory, reuse the secrets like the various keys and passwords, and corrupt the code. Generally speaking, the more we can run in hardware the better."
The document also goes into detail on Google's safe coding and code review systems, operational security practices, identity management, storage security and many other areas.
While the full version is well worth a read, the document notably includes a "CIO-level summary" at the beginning. That's a clear indication of its true target audience, as Google looks to ramp up and expand the breadth of its enterprise cloud business under the leadership of Diane Greene.
24/7 Access to Constellation Insights
Subscribe today for unrestricted access to expert analyst views on breaking news.



